2024-06-22 Self hosting Amazon Linux 2023
And overcomming absent credentials
Goal
Self hosting an instance of Amazon Linux 2023
Background
Amazon provides Qcow2 images for Amazon Linux 2023 but there are no credentials published. We want to reset the credentials of the image, on an unencrypted image
Method
First download the image, it’s not a normal file that is downloaded so we create a new directory and download it:
mkdir /var/lib/vz/template/qcow
cd /var/lib/vz/template/qcow
wget https://cdn.amazonlinux.com/al2023/os-images/2023.4.20240611.0/kvm/al2023-kvm-2023.4.20240611.0-kernel-6.1-x86_64.xfs.gpt.qcow2
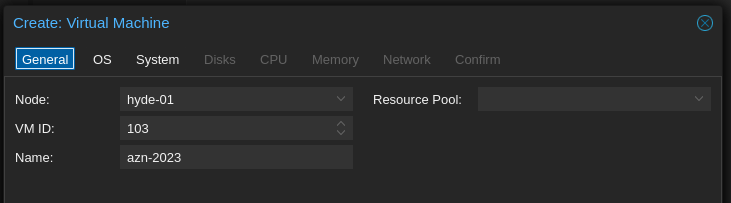
Next we create a new VM in proxmox but without a disk, keeping track of it’s name:
Then on the Proxmox host import the Qcow2 disk to the computer:
qm importdisk 102 al2023-kvm-2023.4.20240611.0-kernel-6.1-x86_64.xfs.gpt.qcow2 local-btrfs

Back on the proxmox host, we need to mount the raw disk, jump into a chroot on that disk, and run passwd on the ec2-user
#enable nbd
modprobe nbd max_part=8
#create a simulated local block device out of the raw image
qemu-nbd --connect=/dev/nbd0 --format=raw /var/lib/pve/local-btrfs/images/102/vm-102-disk-1/disk.raw
#determine which partition (look for the large file system)
fdisk /dev/nbd0 -l
#mount the correct partition
mount /dev/nbd0p1 /mnt/azn/
#enter the mount point and chroot
cd /mnt/azn/
chroot .
#override password in chroot jail
passwd ec2-user
#exit chroot jail
exit
#leave mount and umount block device
cd ../..
umount /mnt/azn
Then start the image, open the machine console and login with your new password

authorized_keys file via ssh